All three of the three techniques of choice jacking defeat Android Jose Jacking Jacking. One of them also works against these defenses in Apple devices. In all three, the charger works as a USB host to mobilize the verification indicators on the targeted phone.
The attacks then exploit various weaknesses in the OS, which allow the charger to inject “input events” in an autonomous injection that can insert the text or click buttons indicate on the screen as the user has done it directly into the phone. In these three, the charger eventually receives two conceptual channels on the phone: (1) an input that allows the consent of the user to accelerate and (2) the connection of the files that can steal files.
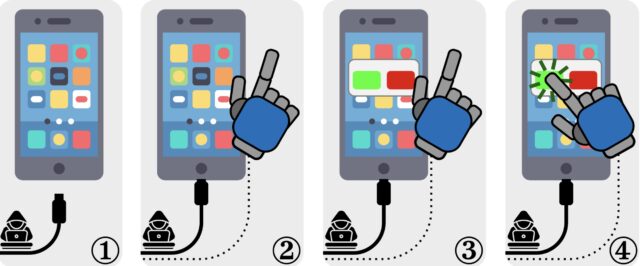
An example of election jacking attacks. (1) The affected device is connected to a malicious charger. (2) The charger sets an additional input channel. (3) Charger launches data connection. This requires user consent to confirm. (4) The charger uses the input channel to fake the consent of the user.
Credit: DraSch Bachar et al.
It’s a keyboard, it’s a host, it is both
Apple- and Google’s underlying juice Jacking Yetfius, in the electoral jacking variations, begins as a charger USB keyboard or similarly peripheral device. It sends the keyboard input to the USB that requests easy key presses, such as arrows up or down, but even more complex key combinations that mobilize the settings or open the status bar.
The input sets up a Bluetooth connection from the other ManteOred keyboard hidden inside the malicious charger. The charger then uses USB power supplyUSB-C connectors have a standard available that allows devices to either other tools or to receive electricity, depending on the messages they exchange, this process is known as USB PD data roll exchange.
An artificial choice jacking charger. Bilateral USB lines allow to change the role of the data.
Credit: DraSch Bachar et al.
With the charger now working as a host, it triggers a file access dialogue. At the same time, the charger still maintains its role as a peripheral device that acts as a Bluetooth keyboard that approves a file access dialogue.
Complete steps for the attack provided in the Usenic Paper, these are:
1. The affected device is connected to a malicious charger. The device’s screen is open.
2. At a reasonable moment, the charger uses USB PD data roll (DR). The mobile device now works as a USB host, the charger uses as a USB input device.
3. The charger develops input to ensure that BT is active.
4. The Charger Mobile Device visits the BT pair screen in System System Settings to discover.
5. Charger starts advertising as a BT input device.
6. By constantly scanning for newly discovered Bluetooth devices, the charger mobile device identifies the BT device address and launches the pair.
7. Through the USB input device, the charger accepts yes/no pair dialogue appearing on the mobile device. The Bluetooth input device is now connected.
8. Charger sends another USB PD Dr exchange. Now it is USB host, and the mobile device is the USB device.
9. As a USB host, the charger launches data connection.
10. Through the Bluetooth input device, the charger confirms your data connection on the mobile device.
This technique works against everyone except one of the 11 phone models, in which holdout is an Android device operating Vivo Fentch OS, which does not fully support the USB PD protocol. Attacks against the remaining 10 models depend on the hack of the phone model, it takes about 25 to 25 to 30 seconds to set the Bluetooth pair. The attacker then reads access to the file stored on the device until he is connected to the charger.

